If you are using an in-memory distributed cache and your application contains private and sensitive data that you want to secure, you need to ensure that your distributed cache prevents this data from unauthorized access through encryption. NCache provides a rich set of industry-standard algorithms that are nearly impossible to break. With NCache, your sensitive data remains secure, both within the cache and during network transmission.
NCache provides a list of encryption algorithms that you can choose from.
Advanced Encryption Standard (AES)
NCache provides support for the AES algorithm which is an official part of the Federal Information Processing Standard (FIPS). The AES algorithm processes data chunks of 128 bits, using encryption keys of lengths 128, 192, and 256 bits. The supported flavors of AES are listed below.
- AES-128
- AES-192
- AES-256
- AES-FIPS 128
- AES-FIPS 192
- AES-FIPS 256
Triple-DES (3DES) Encryption
NCache also provides support for the 3DES encryption protocol, which processes data key lengths of 128 and 192 bits. You can read the RFC specification document for 3DES on the Internet Engineering Task Force (IETF) website. The following algorithms are supported for NCache encryption:
- 3DES-128
- 3DES-192
Where does Encryption Occur?
NCache data encryption and decryption occur inside the NCache client application process. This means that all data traveling over the network between your application and the cache cluster is already encrypted. Similarly, only encrypted data is stored in the cache store.
Client-Server Connection
When you enable encryption on a cache cluster, you provide an encryption key along with the encryption algorithm provider. This key is kept at each cache server in an encrypted manner. When a client successfully connects to the encryption-enabled cache for the first time, the encryption key and selected encryption algorithm is automatically sent to the client to be used in memory for encrypting/decrypting future requests.
Once requests are made to the cache, NCache client automatically starts encrypting your objects before sending them to the cache. Similarly, it automatically decrypts objects fetched from the cache before delivering them to your application.
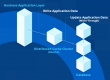
Figure 1 depicts this behavior in 2 simple steps:

Figure 1: Client-Server Encryption Behavior on Connection
Encrypted Data In-Transit and At-Rest
If you’re handling sensitive data in NCache, you can rest assured that data is encrypted and secure from unwanted access at all stages of its life. Please note that if you only want to encrypt data in transit, you can use TLS. However, if you need both or only need encryption for data at rest, you should use encryption.
Data from Client to Server
Once the encrypted key resides at the client-end within memory, any data that has to be sent to the cache is encrypted using the key. Generally, the data is first serialized, encrypted, and compressed (if compression is enabled). Encryption of data at the client-end before being transmitted means that the data is encrypted in transit. This ensures anyone eavesdropping on this connection will not be able to fetch any sensitive data.
Data At-Rest
Once the data is added to cache, the data is stored in its encrypted form, so it is secure even at the cache end.
Data Within Cluster Nodes
Within the cache cluster, data is encrypted during server-to-server state transfer or replication. So, it is still encrypted in-transit.
Figure 2 shows how data is encrypted from client to server:

Figure 2: Encrypted Data In-Transit and At-Rest in NCache
Client Cache
A client cache is a local cache residing on the same box where the application is running. This is synchronized with the remote clustered cache to improve performance for read operations. In the case of a client cache, encryption is not configured explicitly on the client cache. If the clustered cache (L2 level cache) has enabled encryption, then the client cache is encrypted too. If there is no encryption enabled on L2, the data will be added to the client cache without encryption.
Client API
The encryption/decryption behavior for NCache client API is handled automatically while ensuring all data in transit is encrypted and is only decrypted where it needs to be processed.
- Client Connection: When the client connects for the first time, it gets the encryption key and specified algorithm in an encrypted form. This is used to encrypt/decrypt data when needed.
- Adding Data to Cache: For APIs that add data to the cache like Add/Insert etc., the data is encrypted at the client end before traveling over the network. At the cache end, the data is stored in encrypted form.
- Fetching Data from Cache: For APIs that fetch data from the cache like Get/GetBulk/Loader/Queries etc., the data is in the cache in encrypted form, it travels to the client in encrypted form, and the data is decrypted at the client end.
- Events: For the events that require sending data/metadata back to the client where the server data is encrypted, the data is encrypted in transit and decrypted at the client end.
Metadata of Cache Items
Cache items are added with metadata like Groups, Tags, and Named Tags, which define how data is indexed. Both the data and metadata are encrypted at the client end before being sent over the network. At the server-end, the data remains encrypted, but the metadata is decrypted for indexing on the server nodes.
Data Structures in Cache
NCache provides support for data structures. As data is added to the cache, it is encrypted before being added to the data structure. Similarly, when the data structure is fetched from the cache, the data is decrypted at the client end and can be used as needed.
Server-Side Features
As with client-side features, the encryption/decryption mechanism for NCache server-side features is handled automatically on the nature of the feature:
- Read-thru: Irrespective of how and where data is loaded from, if encryption is enabled on the cache, the data will be added to the cache after being encrypted, serialized, and compressed (if compression is enabled).
- Write-thru: The data in the cache is encrypted, but for sending data to be persisted to the Write-thru source, it has to be decrypted so it is stored as is.
- Cache Loader: Since Loader uses the public API, if encryption is enabled on the cache, the data being loaded will automatically be stored in encrypted form in the cache.
- Entry Processor: If the Entry Processor is invoked to process an object, the object is decrypted at the server as all processing takes place at the server-end.
Enabling Encryption
You can enable encryption through NCache Management tools without any programming effort on your part. Encryption has to be enabled on cache start so that all data is homogenously encrypted. You can learn more about this in our docs on Configuring Encryption.

Figure 3: Configuring Encryption in NCache
Additional Security Features in NCache
Apart from encryption, NCache also provides secure communication through SSL/TLS and supports HTTPS for NCache Management Center in Windows and Linux using TLS certificates. Moreover, it ensures your cache environment is secure at the cache API and node management level by providing LDAP integrated authentication and authorization.
Conclusion
Data is undoubtedly the new currency, and cybersecurity is the gold standard. NCache understands the critical importance of securing your data and offers a comprehensive suite of security features to ensure compliance with the latest algorithms. However, since encryption and decryption are CPU-intensive processes, they should be employed selectively to avoid impacting performance.