Configure SSL/TLS Encryption in NCache
Note
This feature is only available in NCache Enterprise Edition.
NCache provides the facility to enable TLS/SSL encryption (using TLS 1.2) over the network to ensure secure data exchange takes place between the server and the authorized client.
Users can hence enable any issued or self-signed SSL certificate to enable connections of the client with NCache server. This guarantees encrypted data transmission by default. Moreover, NCache provides the flexibility of optionally providing the certificate over the client machine.
Pre-requisites
Before issuing a SSL certificate in NCache, the following prerequisites must be considered:
The certificate must have a private key. For creating certificates, refer to this blog on Generating Self Signed Certifcates on Windows.
The private key must be exportable, to be exported to all nodes including the client machine.
Before enabling SSL security, make sure that:
Cache and client processes have been stopped.
The certificate is installed in the Trusted Root Certificate Authorities store in Microsoft Management Console. If it is in the Personal folder, drag-and-drop the certificate to the Certificates folder in Trusted Root Certificate Authorities.
If the client certificate is to be made optional, please refer to the Property table below for detailed prerequisites in this case.
Enabling SSL Certificate in NCache
The certificate can now be enabled for NCache through Registry Editor in the key location HKEY_LOCAL_MACHINE\SOFTWARE\Alachisoft\NCache.
Right-click on NCache -> New -> Key.
Name this key “TLS”.
Create the following properties of the certificate, by right-clicking on TLS -> New.
| Property | Type | Description |
|---|---|---|
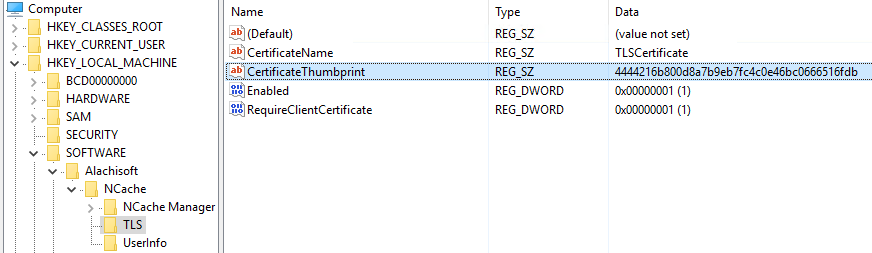
CertificateName |
String |
Name of the certificate to be enabled for NCache SSL security. Steps to obtain the value have been specified after the table. |
CertificateThumbprint |
String |
Unique identifier for each certificate. Steps to obtain the value have been specified after the table. |
Enabled |
DWORD |
Boolean value to enable or disable SSL certificate. Enable SSL by setting the value to 1. |
RequireClientCertificate |
DWORD |
Boolean to specify whether the certificate is required at client end or not. Note the following pre-requisites for each case:RequireClientCertificate = 1:The SSL certificate should exist on both server and client. The value for this property must be 1 on both server and client. RequireClientCertificate = 0:It is not mandatory for the SSL certificate to exist on the client machine; however, the issuer of the SSL certificate must have any other certificate issued on the client in the Trusted Root Certificate Authority. This creates “trust” between the client and server. |
To obtain the CertificateName and CertificateThumbprint values of the certificate:
Go to Microsoft Management Console by clicking Start and typing MMC in the dialog box.
From the File menu, click Add/Remove Snap-in.
Click on Certificates and then select Add.
On clicking Add, the user is asked to choose between the user, system and computer account. Make sure to choose the My User Account.
Once the certificates are added, open the Trusted Root Certificate Authorities folder in the standard way.
Double-click on the certificate name.
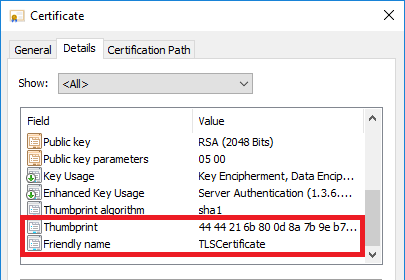
Click on the Details tab.
Click on Friendly name, this value is the CertificateName.
Click on Thumbprint.
Copy the Thumbprint value and edit it to remove spaces from the value. This value is to be provided to the CertificateThumbprint property.
- If the certificate is required on the client machine, set the value of RequireClientCertificate to 1, complying to the relevant prerequisites.
The TLS key under Alachisoft will look like this:
Important
Make sure that the registry values are consistent on all server and client nodes to ensure connectivity and homogeneity of cluster.
Once the desired properties are set, restart the Cache and Client processes. Make sure that NCache service is running under the same user which was used to import the certificate.
Export the certificate (through the standard way of exporting certificates) to all server nodes in the cluster (and all client nodes if client certificate is required) and perform the same steps to enable SSL security on all nodes.
Note
Once the certificates have been enabled, make sure that:
- NCache service is running under the same user which was used to import the certificate.
- All client applications run on 64-bit machines.
Verify Successful Client Connectivity Through TLS
- In order to verify successful client connectivity through TLS, you can run the Test-Stress cmdlet using Windows PowerShell Tool. Following example runs
Test-Stresson the cache named myPartitionedCache.
Test-Stress -CacheName myPartitionedCache
- You can also verify this using Microsoft Network Monitor. In case TLS is enabled, the Protocol Name of the process PowerShell.exe on running
Test-Stresswill be TLS.
Troubleshooting
Client connectivity through TLS can be failed due to the following reasons:
If the registry entries are missing, the connectivity might fail. Make sure that all the entries are made in the registry.
If NCache Service has different user credentials than the user which was used to import the certificate.
Certificate will be invalid if the thumbprint value provided to the CertificateThumbprint property is not correct.
If the values of the properties are not same in the client and server machine, you receive an error saying "Decryption Operation Failed".
See Also
Configure Security for Cache Management
Configure Security for Cache
Configure Security for Client Nodes
Configure Encryption for Cache