Securing cached data in a multi-data center environment is paramount. There’s no denying that. But is securing data enough to ensure you have secured your cache environment? I’d beg to differ; it’s not nearly enough. Along with data security, you need to make sure your cache and server nodes are safe from unauthorized access as well.
For this exact reason, NCache, an in-memory distributed cache, provides security for cache and node operations to secure the environment you are working in. Although security is an optional feature, it becomes absolutely demanding when you know you have open user access to your cache. Here, I’m going to try to dissect how NCache security works. There are mainly two basic steps involved in this process.
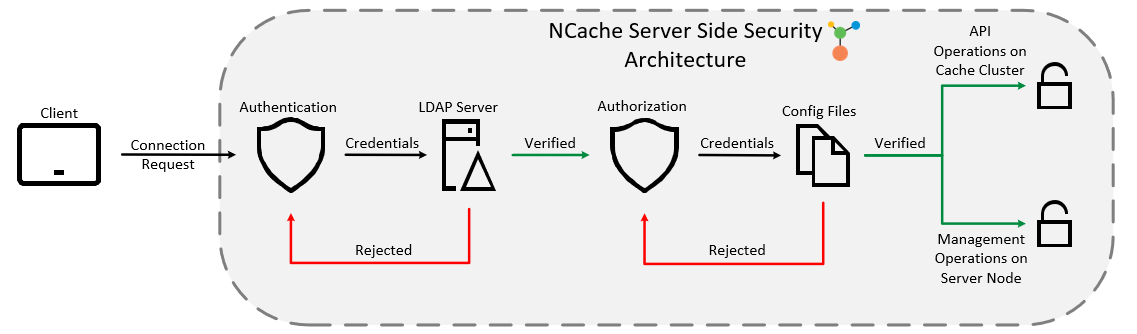
- Figure 1: NCache Server Side Security Architecture
NCache Details NCache Security-Docs NCache Security-Blog
1. User Authentication
Authentication ensures whether the client that’s trying to connect to the cache is in fact an actual user of your domain or not. NCache uses LDAP Service Providers for authenticating all incoming client connection requests.
For Cache Level Security, you have to provide an LDAP provider against which all client connections are authenticated. But when we discuss Management Level Security, aka Node Level Security, you need to make sure that for every node, you provide the same LDAP provider assuming that the environment you are working in is homogeneous. This is done to make sure that the administrators on all nodes remain the same.
2. User Authorization
After successful authentication, we understand that a specific user is an authentic user of that domain, but does that user have the rights to perform operations on the cache cluster or a server node? Authorization is the way to identify that. The declaration of what the authenticated user can do on your cache/node is the responsibility of authorization. If a user is registered against a cache or a node, then it has the authority to perform all API or managerial operations on the cache/node.
NCache Details NCache Security-Docs NCache Security-Blog
NCache, by implementation, has two levels of security in Authorization.
Security Behavior in Clustered Cache
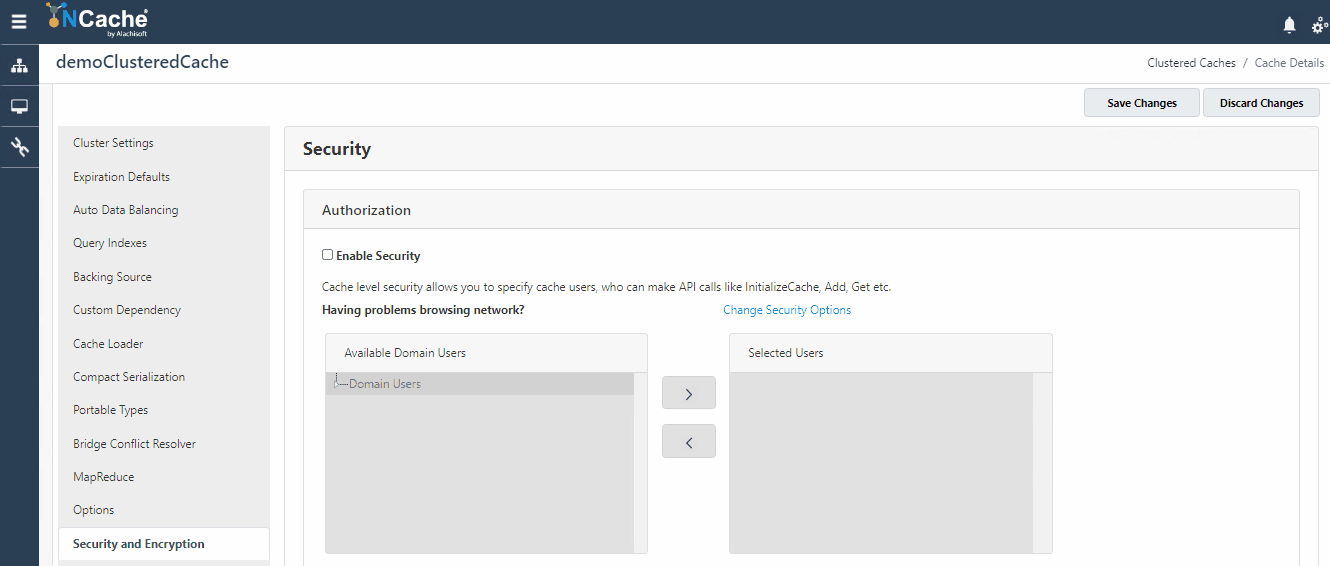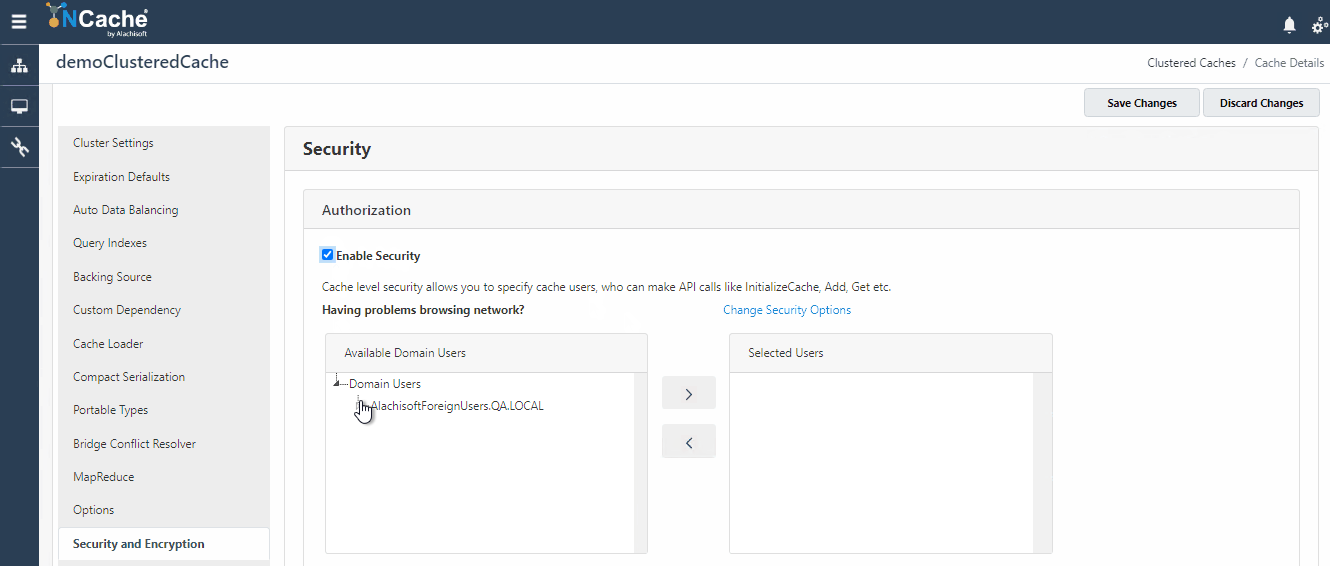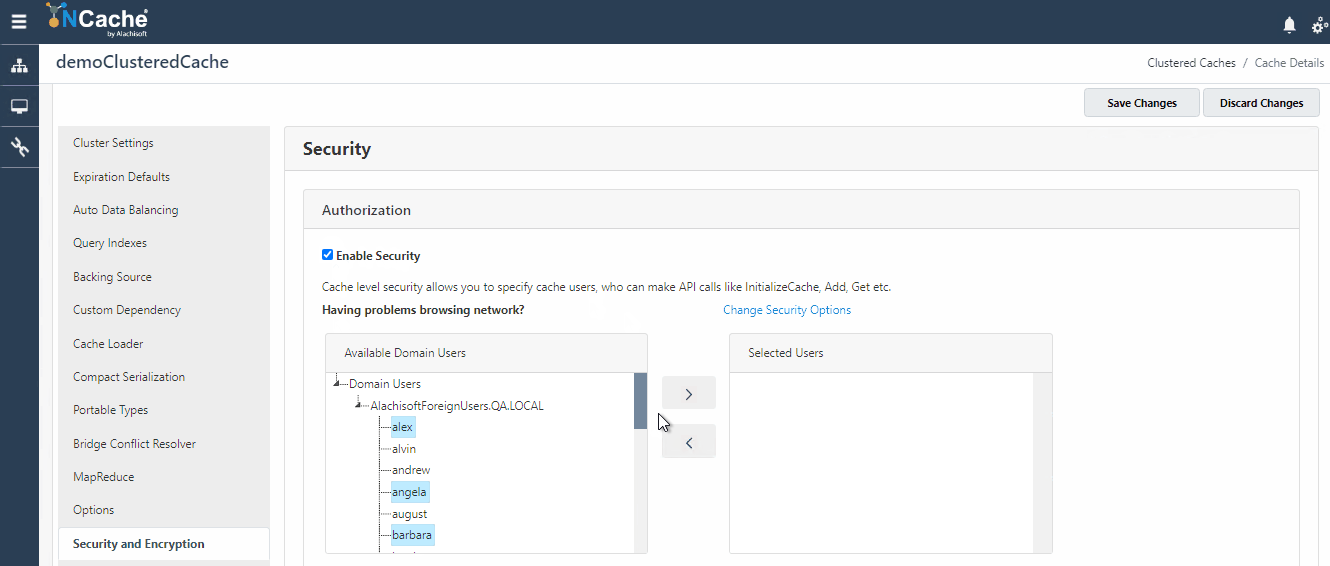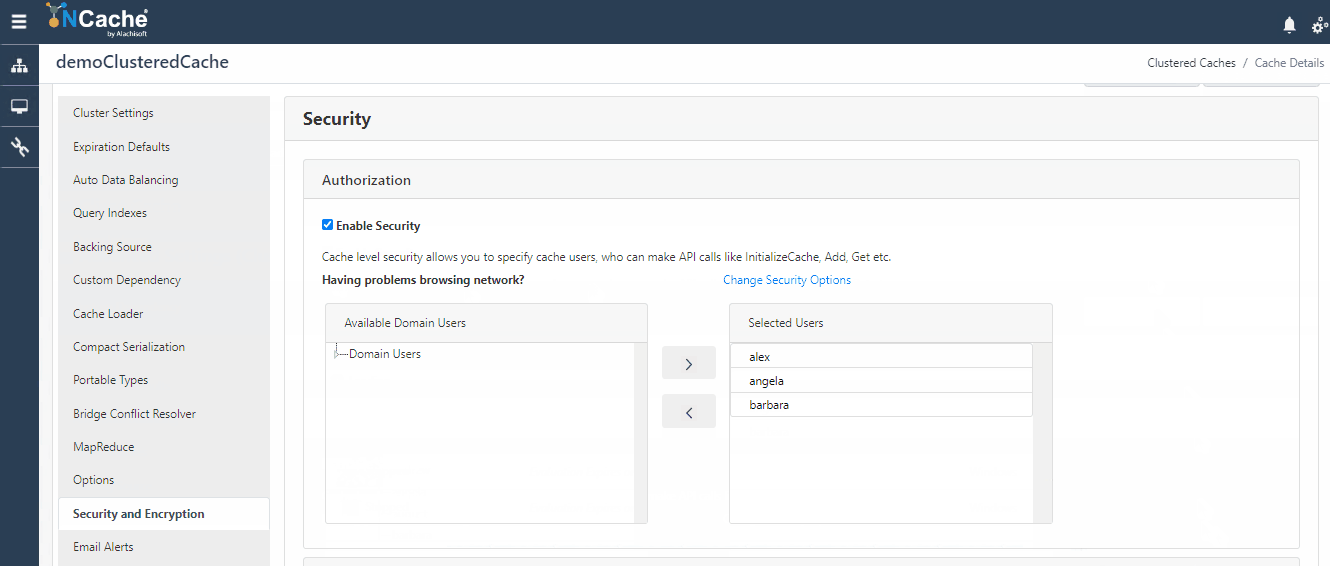
Cache Level Security, most commonly known as Cache API Level Security ensures that your cache is secured from any unauthorized access. All the users trying to create a connection with the cache through NCache API are first authenticated against cache level security before being granted access to perform any operations on the cache. To learn how to become an authorized user for a cache, follow our help on Configure Security for Cache Cluster. The users registered against cache level security are populated in your cache config file which is used by the NCache server for authorization.
- Figure 2: Configure Users for Cache Level Security in NCache
Security Behavior in Server Node
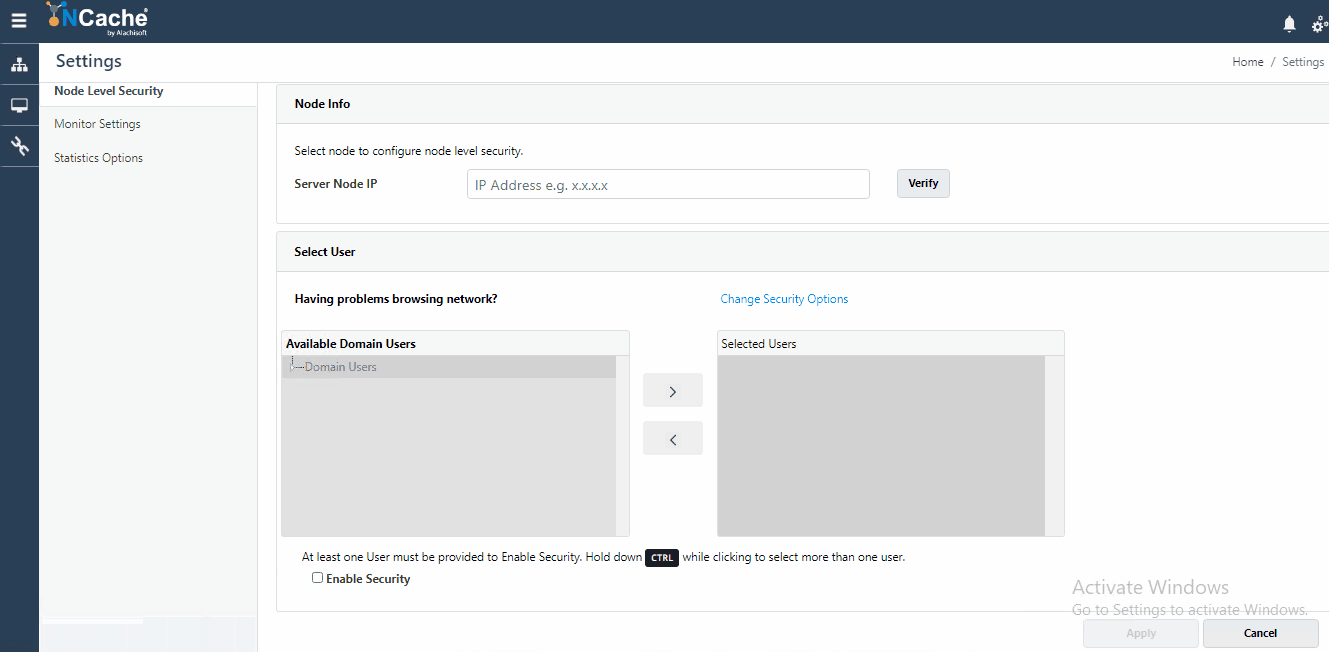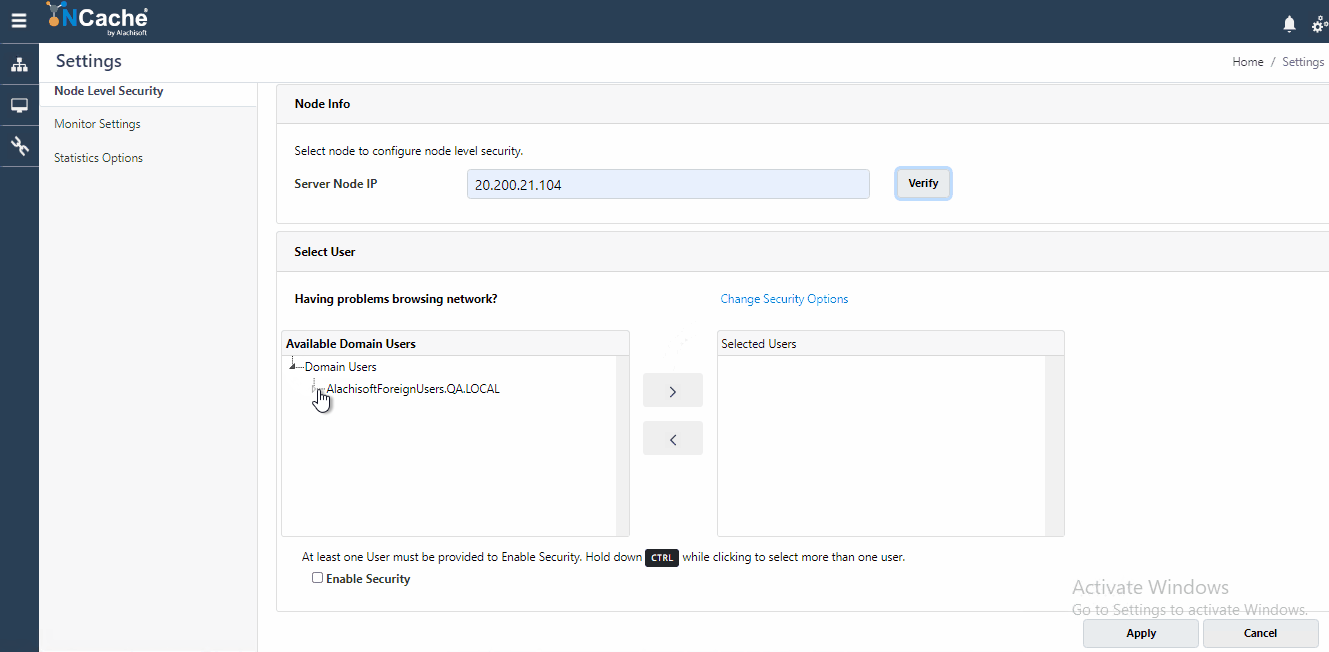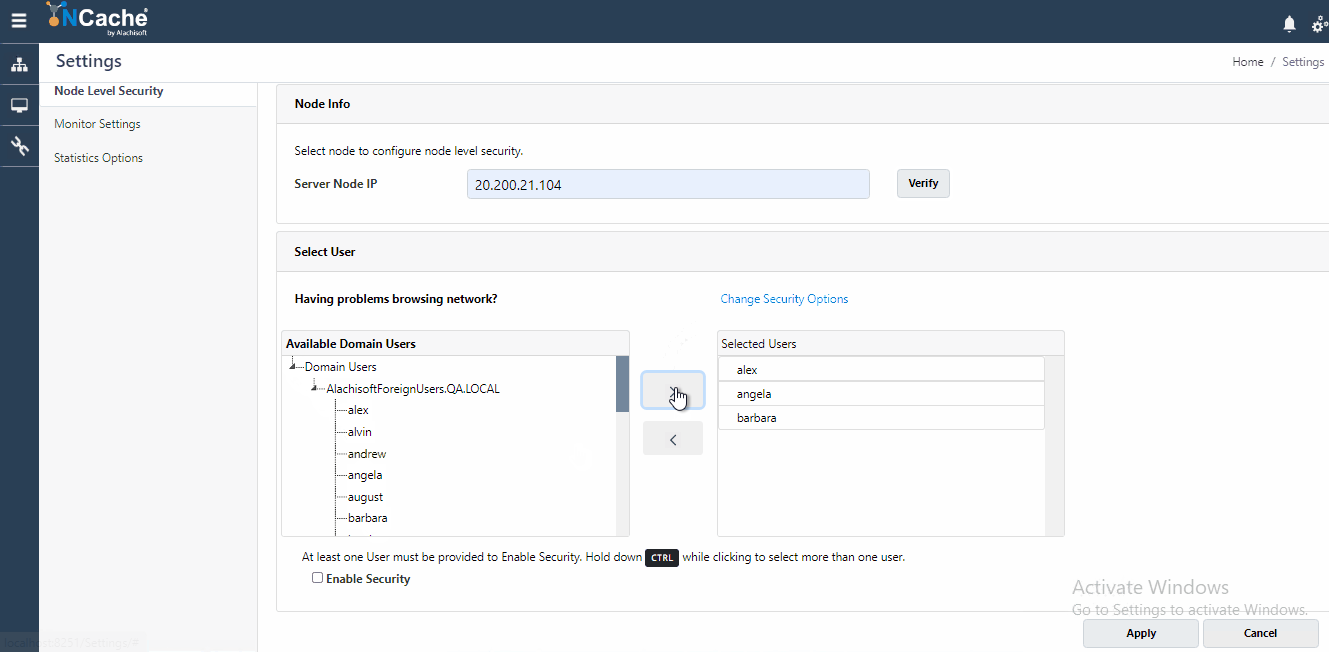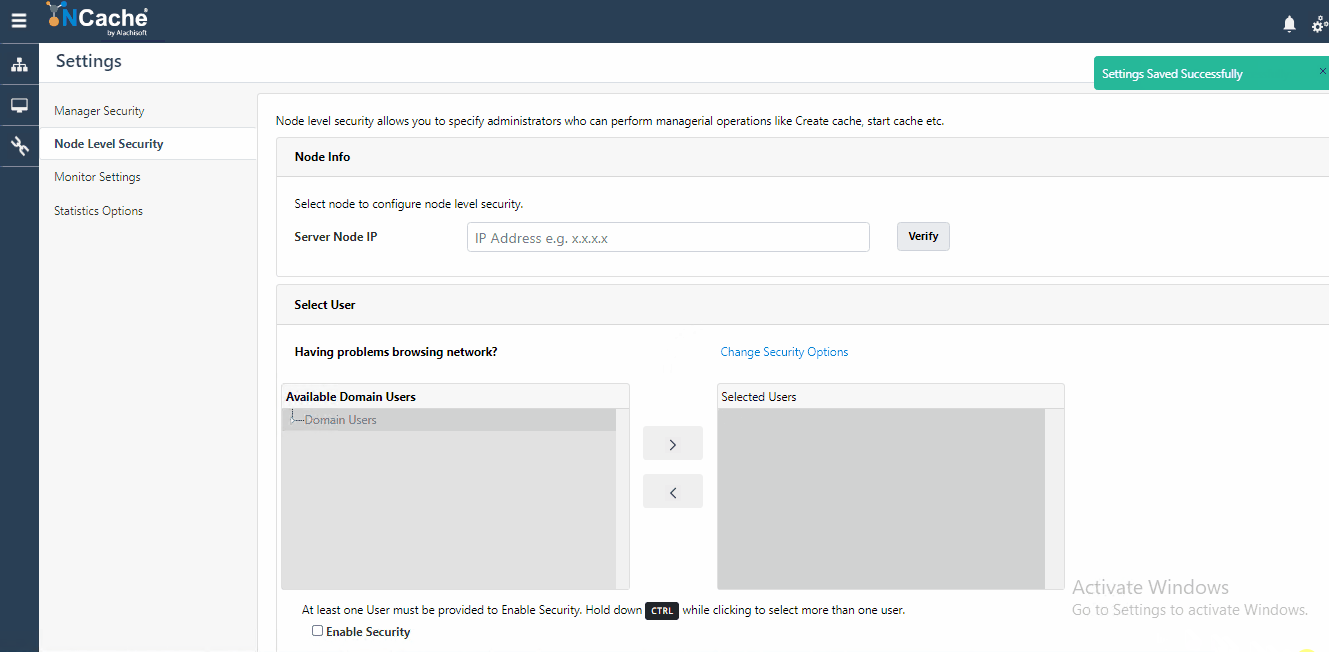
Node Level Security, also known as Management level security validates all authorized users who have access to perform any management and configuration operation on a server node. To enable this security, you need to be an administrator on that node. To understand how you can be an admin on a node, refer to our documentation on Configure Security for Cache Server Nodes. The users you register against node level security get populated in security config file which is used for authorizing incoming connection requests.
- Figure 3: Register Users for Node Level Security in NCache
NCache Details NCache Configure Security NCache Security-Blog
Security Behavior in Client Cache
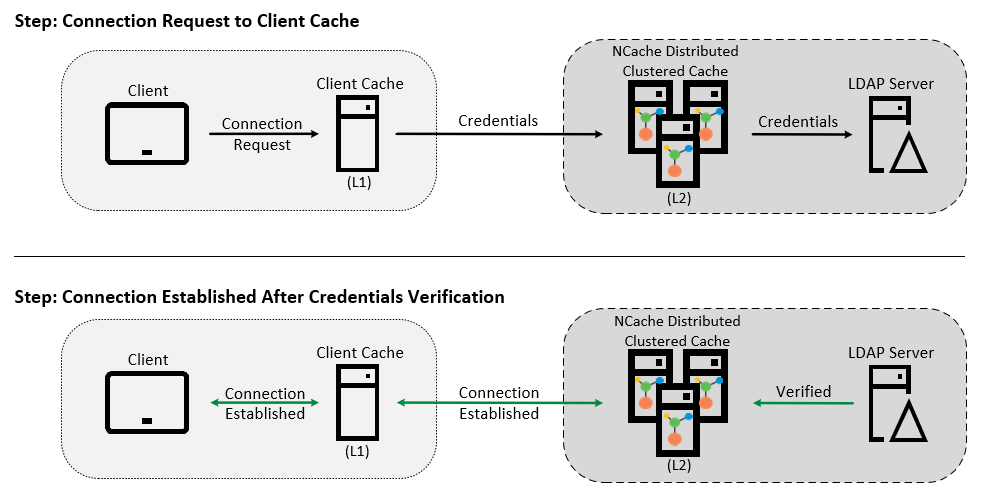
NCache amidst all these security implementations also enables security for your Client Cache. The way NCache secures access to your client cache is simple:
-
- User sends a connection request to your Client Cache (L1) in the attempt to connect to your Clustered Cache (L2).
- L1 uses those user credentials to request a connection with L2.
- If those credentials are authenticated by L2, a secure connection is established and L1 connects to the client.
From this you can tell that:
-
- You don’t have to specifically configure security for your client cache.
- Your Client Cache does not need to authenticate a user connection by itself.
- Your Client Cache is responsible for getting L2, your remote Clustered Cache to authenticate the incoming connection request.
This is how NCache secures the data stored in your Client Cache:
- Figure 4: Client Cache Security Behavior in NCache
Additional Security Implementations by NCache
You might be wondering how securing your caches is enough to have a secure environment for your application. Just to address your concerns, I will briefly share some additional security features provided by NCache that secure your data here:
Data Encryption in NCache
Data encryption lets you encrypt sensitive data that you want to store in NCache. NCache supports many strong encryption algorithms that not only secure your stored data but also ensure that the exchange of data between servers is secured too. Get a detailed idea of how NCache encrypts data from our blog on Diving Deeper into Encryption in NCache.
Secure Connections Using SSL/TLS
To secure your data transfer between NCache servers and clients, NCache provides support of SSL/TLS 1.2. These encryption techniques use an encryption certificate that is shared with your server and the client to secure your network. This certificate contains all the information needed to encrypt and decrypt the secured data. To know more about how this works, refer to our blog on SSL/TLS Configuration in NCache Made Simple.
NCache Details NCache Security-Docs NCache Encryption-Docs
Let’s Wrap This Up
NCache not only allows you to secure your data through encryption but also allows you to secure the actual cache environment that you are working with. NCache provides multi-level security that keeps all the uninvited users away from your cache, as they should be; like pineapple on pizzas!